The number of internet-connected devices in homes has been growing. It’s increased exponentially over the last decade. A typical home now has 10.37 devices connected to the internet. PCs and mobile devices make up a little over half of those and the rest are IoT devices. IoT stands for Internet of Things. It means any… Continue reading Home Security: Why You Should Put IoT Devices on a Guest Wi-Fi Network
Category: Blog
If you’re under pressure to take urgent action – stop and think
Phishing scams are one of the biggest security threats to your business right now. A massive 83% of organizations said they suffered successful attacks last year. And with just under a third of phishing emails being opened, the chances that someone in your business will be fooled are high. But to make matters more difficult,… Continue reading If you’re under pressure to take urgent action – stop and think
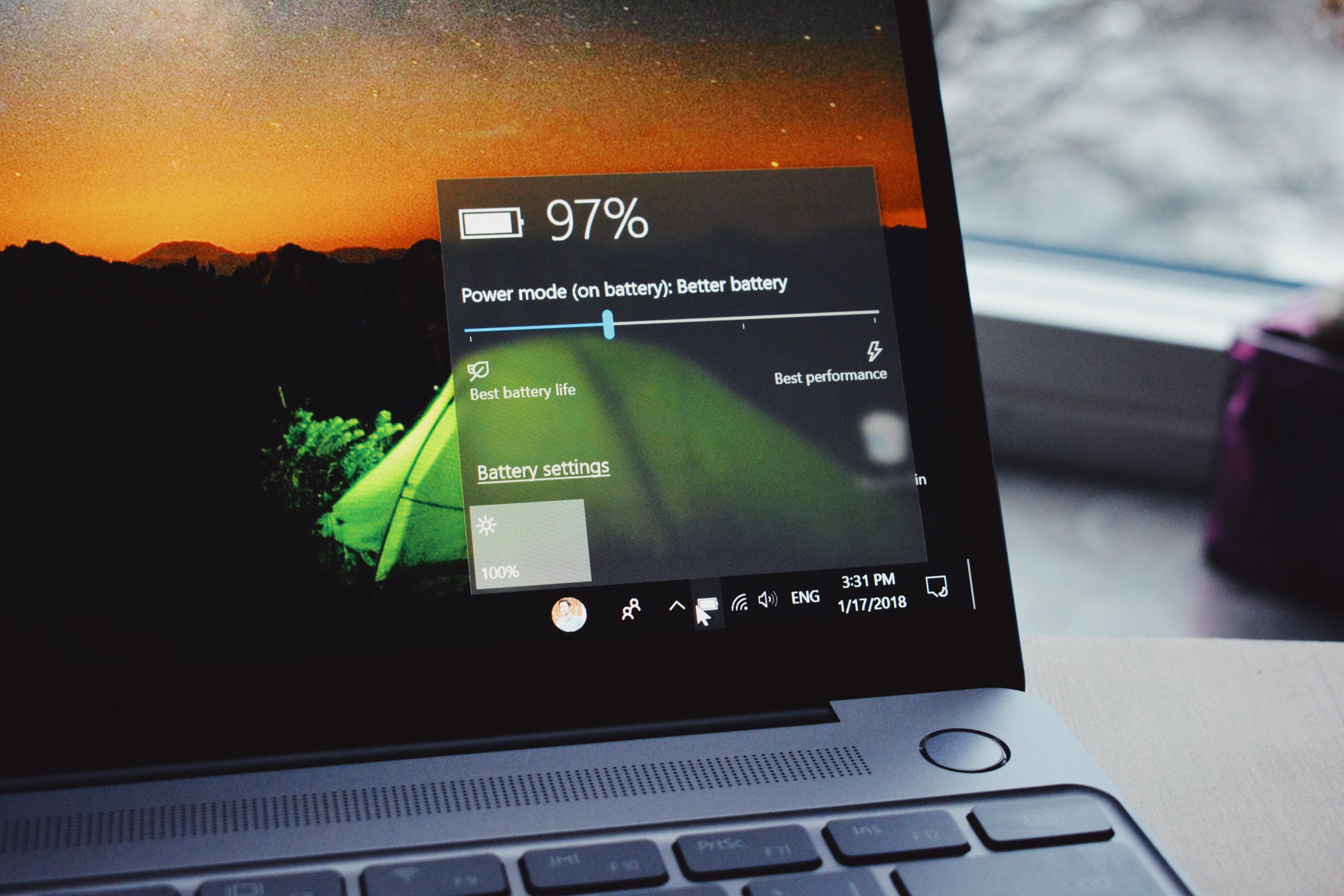
Get More Unplugged Laptop Time with These Battery-Saving Hacks
One of the big draws of a laptop computer is that you can use it anywhere. You don’t need to have it plugged in all the time because it has an internal battery. Your laptop may start out with several hours of battery life when you first buy it. But the lifespan can get shorter… Continue reading Get More Unplugged Laptop Time with These Battery-Saving Hacks
Why Planning for a Cyber Attack Is Your BEST Defense and Will Save You From Bankruptcy
In the disaster preparedness world, acting “as if” is a mantra. This means acting as if a certain crisis incident is bound to happen. For example, acting as if your small or mid-sized business will definitely be attacked instead of assuming you’re too small for a hacker to bother with. 50% of small businesses that… Continue reading Why Planning for a Cyber Attack Is Your BEST Defense and Will Save You From Bankruptcy
5 Exciting Ways Microsoft 365 Can Enable the Hybrid Office
“Hybrid office” is the new buzzword you’ll hear used in business discussions. It’s the mix of having employees both working at the office and working from home. This has become more than a buzzword and is now the reality for many companies. There was a survey of employees with remote-capable jobs. The survey found that… Continue reading 5 Exciting Ways Microsoft 365 Can Enable the Hybrid Office
Is working from home really good for your business?
Working from home. Or remote working, as it’s now called. It’s the big thing in business, isn’t it? And some people love it. They’re happier working where they want, and when they want. And that makes them more productive and less likely to leave. But have you stopped to consider the downside to remote working?… Continue reading Is working from home really good for your business?
IT Guys LOVE When Your Systems Are Down
Why on earth would an IT service provider want your systems to go down? Isn’t that what they’re supposed to keep from happening? Yes, in theory. And yes if they’re a reliable and good managed services provider (MSP). But unfortunately, not all in the IT biz are. Some MSPs are just looking to make money… Continue reading IT Guys LOVE When Your Systems Are Down
Which Form of MFA Is the Most Secure? Which Is the Most Convenient?
Credential theft is now at an all-time high and is responsible for more data breaches than any other type of attack. We’ve seen a rise in data breaches for small businesses in Houston lately. How do you protect your online accounts, data, and business operations? One of the best ways is with multi-factor authentication (MFA).… Continue reading Which Form of MFA Is the Most Secure? Which Is the Most Convenient?
If You Don’t LIKE or TRUST Your IT Company With Your Bank Account, FIRE Them NOW
Computers, networks, and firewalls might not seem very personal, but they are. You need to be completely comfortable and familiar with the people that take care of your technology for you, otherwise, your business as a whole could suffer. Would you trust your IT company with your bank account login? If the answer is “No,”… Continue reading If You Don’t LIKE or TRUST Your IT Company With Your Bank Account, FIRE Them NOW
Top 5 Mobile Device Attacks You Need to Watch Out For
Smartphones and tablets are often the preferred device for communications, web searching, and accessing many types of apps. They’re more portable and can be used from anywhere. We’re seeing the takeover of many activities that used to be performed on traditional computers. A lot of our clients based here in Houston have started using tablets… Continue reading Top 5 Mobile Device Attacks You Need to Watch Out For